
From fright to delight! Spooky Cybersecurity tricks and Ethical Hacking treats
For many of us, October is a month of pumpkins, spooky decorations, spider webs, skeletons, and creepy costumes. While we're on the subject of scary things, it is a good time to remind you that October is also the Month of Cybersecurity Awareness with several campaigns around the globe that aim to raise awareness about the importance of online security. In Europe, there is the European Cyber Security Month (ECSM), the National Cyber Security Awareness Month (NCSAM) in the United States and the Cyber Security Awareness Month (CSAM) in Canada. All these initiatives are focused on providing resources for educating and informing people, organizations and employees about online security and how to protect personal and professional data.
Independent IT specialists at Reviewedbypro and many other sources indicate that hacking skills aren’t used only for malicious activities. Hackers are also used by many companies who want to increase their security and keep malicious attackers away from their systems, servers, networks and software.
So, just in time for Halloween, we will give you a good scare with these haunting cybersecurity facts and information that will make you sit up with a scary feeling in your bones. And the worst part is that the risk of a cyberattack has increased for companies of all sizes and across all industries over the past couple of years.
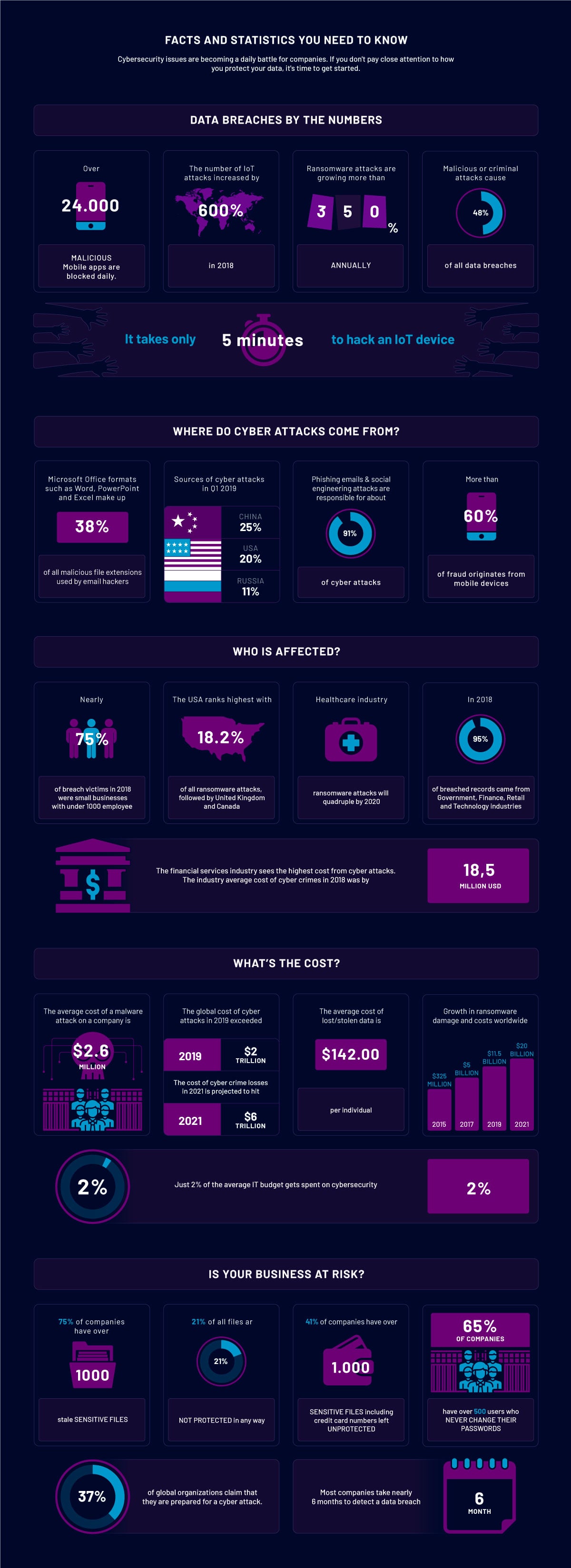
Now that you've reviewed these alarming statistics, we want to let you know that there is a way to protect your business from cyberattacks and that’s through ethical hacking. Below we will shed some light on why businesses need, now more than ever, to hire ethical hackers to protect their systems and network.
What is "Ethical Hacking"?
Hackers are usually seen as dodgy characters in hoodies, bent over a computer in the dark, trying to invade foreign systems and do as much damage as possible. This kind of hackers is also known as "Black Hat Hackers". But on the other hand, there is something like "Ethical Hacking". Ethical hacking, also known as "Penetration Testing" or "White Hat Hacking" refers to detecting software or hardware vulnerabilities that can allow criminals to access systems and then report the issues to customers and developers so they can fix the problem before the security risk becomes real harm. "Gray Hat Hackers" are often operating for the common good, they may violate ethical standards or principles such as hacking groups they are ideological against or may launch protests against them. "White Hat" and "Gray Hat" hackers can both be defined as "ethical" hackers.
Many large companies, such as IBM, Telekom, Facebook, Microsoft, Google or government agencies employ entire hacker teams to discover security holes in their networks or services. This way vulnerabilities can be resolved before they are found by criminals.
How do ethical hackers work?
First of all, a comprehensive safety analysis is important as part of the company's security management. It aims to detect threats through penetration tests and to identify weaknesses and vulnerabilities that include malicious code, as well as the lack of functionality that can lead to security breaches. If vulnerabilities are found, an ethical hacker will document the issues and provide a plan on how to fix the problems.
What vulnerabilities can be detected by simulated attacks?
In principle, almost all weak points can be detected. Of course, vulnerabilities that provide access to sensitive data, such as unauthorized modification of configuration settings or phishing mails, insecure configuration of networks, hosts or devices, flaws in encryption or authentication are particularly important.
Can penetration testing interfere with ongoing IT operations?
Depending on the nature of the work, ethical hacker’s intervention may lead to disruptions of IT operations. But it is worth remembering that interruption caused by an ethical hacker will seem minor compared to the stress of dealing with a real hacking or cyber data breach.
Is ethical hacking legal?
Ethical hacking is only permissible if the client expressly agrees that security analyzes and penetration tests are carried out in his company. This declaration should come from an authorized representative in the company - such as the managing director or authorized signatory. With appropriate authority, the IT Manager can also give official approval for ethical hacking.
What should be regulated in the service contract?
It should be regulated when and during which period the penetration tests and analysis take place. Other important points include risk classifications of the tests, techniques used (network access, physical access, social engineering, etc.), as well as information on the scope of the tests. A secrecy clause must also be included, as ethical hackers may gain insight into confidential company information.
What legal details do companies have to consider?
The client may only give his consent for areas that are under his jurisdiction. There must be clarity about the subject of testing on both sides before the security analysis and penetration tests begin. This is especially important when dealing with systems operated by third parties - such as parts of the IT infrastructure or the data center.
Is security restored with the removal of all vulnerabilities?
Of course, the IT department will do everything it can to remove any weaknesses that have been discovered together with the ethical hacker. In addition, it must be investigated whether criminal hackers have already exploited the vulnerabilities, for example by installing remote control software to gain permanent control of the system.
What is the demand for ethical hacking?
The demand is growing. As the number of networks increases, fraudulent hacker attacks become more frequent and more dangerous. In the past, ethical hacking services were mainly used by companies working with sensitive data, such as financial services providers or e-commerce providers. However, with the Internet of Things and progressive networking, other sectors must increasingly protect themselves against hacker attacks. Therefore, ethical hacking is an effective way for all companies to detect possible security gaps in their system or product.
How often penetration test should be performed?
Businesses don't conduct penetration tests until after they have encountered a breach or realize that a hacker has already planted a virus in their internal application or system. In order to ensure more consistent servers, systems, software and network security, penetration tests should be performed regularly 1-2 times a year.
How do you recognize a reputable provider?
A good provider always communicates in advance about possible risks for the ongoing operation and insists on a binding contract for both parties. Needless to say, the ethical hacker does not start work until the client has given its explicit consent for the analysis and testing. Look for suppliers who have years of experience in delivering confidential customer commitments.
Unlike trick-or-treaters, cyber criminals don't show up only once a year, so it is vital that your business is prepared and secure. So, here is our treat: a FREE CONSULTATION to assess your security testing needs.
NOTE: The statistics were collected by Indrivo based on the resources such as The Telegraph, Varonis, Statista, Kaspersky, FinancesOnline.com, Cybersecurity Ventures, Data Connectors and CPO Magazine.



